Case for Israel or the US to join the Trustless Computing Certification Body and Seevik Net.
In this long post, we make a detailed case as to why the US and/or Israel, while being the leading western cyber powers, would overall greatly benefit from joining a few leading EU and like-minded nations, to build a new international IT security certification and governance body for digital communications, and an initial set of open IT compliant to such certifications. Such body aims to affirm a long-awaited novel win-win model for reconciling and maximizing both the digital security and privacy of law-abiding persons and their international legitimate lawful access, that is much more effective than the current model.
_____________________________________________________________________________________________
The chronic hyper-complexity and vulnerability of Android and iOS smartphones, their de-facto duopoly in the west, and the wide availability of undetectable tools to hack them, make so that there are dozens of Watergate Scandals going on around the World at any given time, whereby elected officials, opposition and journalists in established democracies are systematically spied on.
As opposed to the original Watergate Scandal that brought down the US president Nixon, this time the spying is way more pervasive, with culprits taking control of a users’ entire digital life for months or years, largely in undetectable ways.
Even worse is the fact that such hacking is largely unattributable. This causes a crisis of trust among political camps and in democratic institutions, when a hack is discovered and it is anyone’s opinion if the culprit was the ruling government, or unidentified enemy nations or cyber criminals, in an unsolvable “blame game”, as reported recently in scandals related to the use of an Israeli spyware in Poland, in India, in Spain and in Israel.
The disastrous insecurity of our digital communications is no different from any other deep-seated problems. Unless we have the courage to recognise the root causes of the problem, and face them head on, we will never know if there might be a substantive solution.
It needs to be said: our digital security and privacy have been sacrificed as collateral damage of the war on terrorism and adversary nations. And with them our freedom, democracy, and ultimately our safety. All because we could not find solutions that would not force us into a zero-sum game.
Arguably, for decades, the US and Israel have directly and indirectly ensured that even the most secure IT and IT security standards are always weaker than they could and should be, kept unfixed and kept hyper-complex - with plausible deniability - in order to protect all western citizens from terrorist and enemy nations, and protect global stability and peace. This model has been overall a huge success so far in protecting us, but has also brought with it devastating collateral damages.
Those wilful weaknesses in all IT were meant by security agencies to remain accessible to “Nobody But Us”, but that has failed spectacularly and systemically. Our elected officials, journalists, and even top US and Israeli political leaders and their close associates, are or can be illegitimately spied on their smartphones - continuously and pervasively, for months and years - by innumerable state and non-state entities that develop, buy, rent spyware to exploit those weaknesses.
But that’s just the start. Even more catastrophic is the fact that (a) this happens at a scale of hundreds of thousands; (b) goes very often undetected for months and years and (c) that attribution is nearly impossible when sophisticated state and non-state actors are involved, especially through proxies, such as private spyware companies. As we’ve learned, even the son of the former Israeli prime minister, or key staff of US presidential candidates - let alone any US and Israeli elected official - can be spied and blackmailed, even by enemies foreign and domestic, with grave damage to nation security.
All this has severely mined democratic institutions, sovereignty, civil rights, and social cohesion in the US, Israel and abroad. It has weakened the trust of allies. It has further mined the credibility of the western democratic model versus authoritarian ones, in the all-important competition for the hearts and minds of citizens of the West, third nations and adversary nations.
Going beyond the “iPhone+NSOs” model of broken-by-design IT and a spyware Wild West?
The current western model to maximize the security of digital communications while concurrently protecting national security - largely hegemonized by the US and Israel - has brought huge successes in countering terrorism and other grave crimes, for which we should be extremely grateful. Yet, such model, which we could call the “iPhone+NSOs” model causes huge collateral damages in terms of civil rights at home and abroad, resilience and trust of democratic institutions, trust between friendly nations, integrity of evidence acquired in cyber-incidence, and credibility of the western democratic model for a digital society.
We believe there is a better way, a better model, that could gradually replace the existing one, based on multilateralism, transparency and battle-tested democratic governance models, procedures, and technologies.
What if ensuring legitimate lawful access and personal privacy are not be an “either-or” choice, or a zero-sum game, but a “both or neither” challenge, solvable by applying the same ultra-resilient trustless democratic safeguards?
Can the current model based on deception, obscurity and a web of obscure un-democratic arrangements among security agencies, be replace with a transparent one whereby a highly democratic and resilient UN-like organization will go all the way to certify radically higher levels of security of IT for sensitive communications, while doing the same for procedural in-person means to enable international legitimate lawful-access?
We invite the US and Israel to join other like-minded nations that have showed interest as founding early governance partners of the Trustless Computing Certification Body (TCCB), and initial end-users of Seevik Net, initial TCCB-compliant interoperable systems and client devices, intended for the most sensitive day-to-day non-classified mobile computing of law-abiding leaders and ordinary citizens alike.
A post-Cold War Crypto AG: multilateral, transparent, for peace, for all and mobile.
In Geneva and Rome, our Trustless Computing Association is building nothing less than a "post-Cold War version of Crypto AG", the de-facto global standard and state-of-the-art for sensitive and diplomatic digital communications during the Cold War, that turned out in 2020 to have been controlled by only two nations.
As opposed to the original one, it will be based on open democratic multilateralism, uncompromising transparency, and an ultra-resilient procedural front-door instead of a technical back-door.
Beyond diplomats, it’ll be available to all with utmost portability and convenience via 2mm-thin standalone devices, carried inside custom leather wallets or in the back of their future smartphones - to finally enable secure, fair, and efficient digital communications and dialogue, within and among nations.
The original Crypto AG provided over 100 nations enormous value in terms of internal and external remote communications reliably secure against interception by any state or non-state actor, albeit at the (witting or unwitting) cost of interception by top security agencies of two nations. Ultimately, Crypto AG was one of the most successful and impactful intelligence operation of the last century, playing a crucial role to make so that a more democratic geopolitical block prevailed over a lesser one.
The original Crypto AG program also proved that digital communications can be made to resist even the most powerful state-grade attackers at relatively moderate R&D costs. Even more relevant, it proved that 3rd-party access to encrypted data and communications can be reliably restricted to intended parties - albeit solely for such ultra-secure IT systems and at moderate scale - contradicting widely shared expert ideas about the impossibility in all cases of a secure-enough "front-door” socio-technical mechanism.
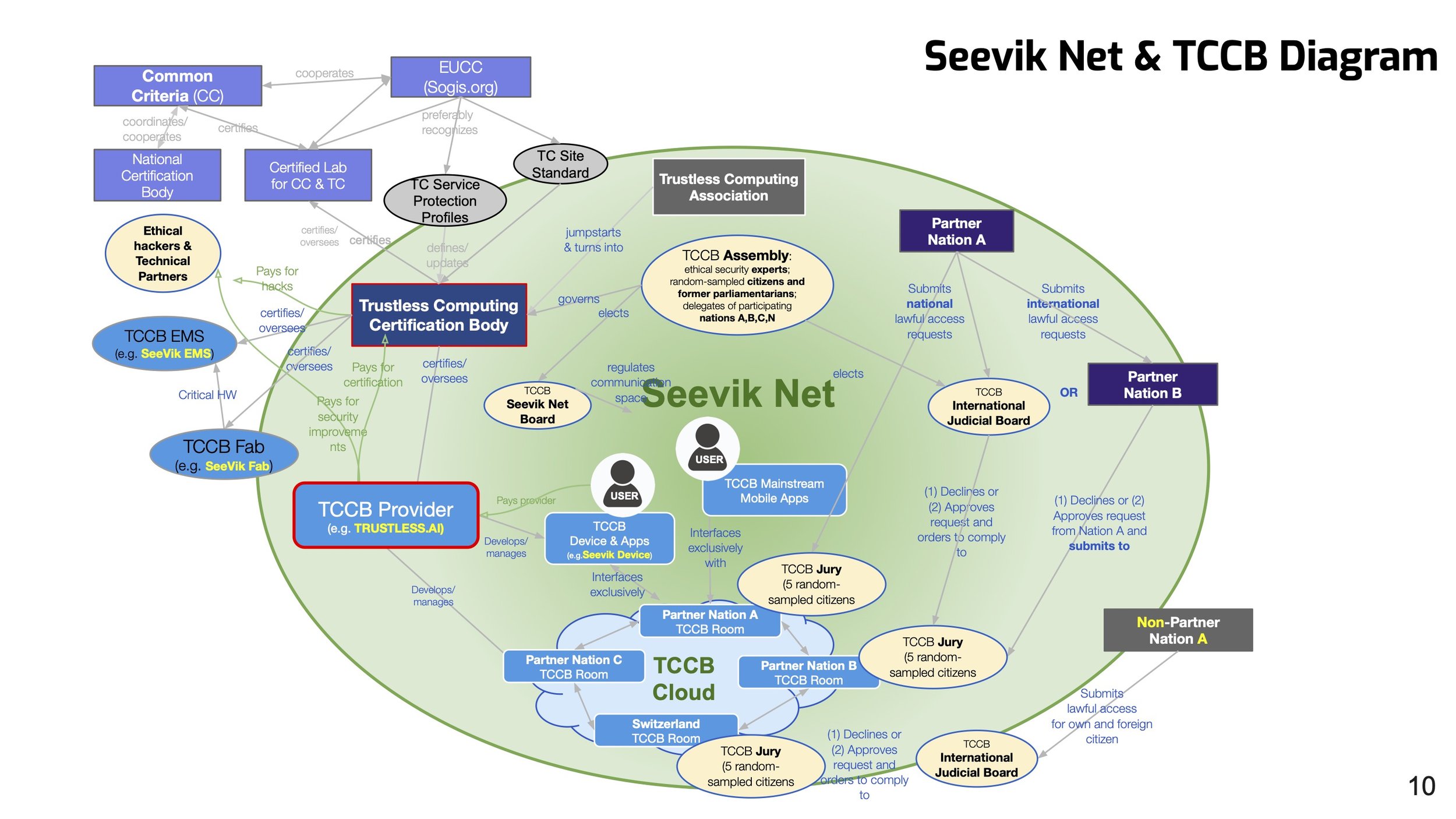
Trustless Computing Certification Body and Seevik Net
TCCB is a new standards-setting and certification body that will certify IT services for human communications aimed to ensure both radically-unprecedented levels of confidentiality, integrity, and democratic control and concurrently safe “in person” international legitimate lawful access mechanism, established last June 2021 in Geneva. Meanwhile, starting from existing open minimized battle-tested IT and unique multinational tech partners, we are building an initial set of TCCB-compliant IT systems - minimal but complete, and mandatorily interoperable - that will constitute Seevik Net, the 1st democratic global human computing sphere and platform, alongside existing dominant platforms.
TCCB and Seevik Net aim to create and regulate a new global democratic digital public sphere - with apps, cloud, and devices, based on existing open systems, that run parallel to mainstream ones and over the open Internet. They aim to radically increase citizens’ privacy, security, and democratic control of their sensitive digital lives; defend democratic institutions from the rise of authoritarianism, at home and abroad, inside and outside institutions; and foster fair and effective dialogue and understanding, within and across nations.
TCCB achieves radically-unprecedented levels of trustworthiness by (A) applying, to both, extreme, battle-tested, and open (technical and organizational) socio-technical safeguards, and checks and balances - the Trustless Computing Paradigms - that are applied to all technologies and processes critically-involved in the entire life-cycle - down to fabrication oversight processes (TCCB Fab), CPU design, and hosting room access (TCCB Cloud) and via (B) a governance model and statute that highly maximizes global democratic accountability, socio-technical competency, and resiliency from state pressures. The statute prescribes that as certain funding goals are reached the association will rename to TCCB, and the permanent governance will be activated.
Seevik Net is being built through startup "spin-in" TRUSTLESS.AI that the Trustless Computing Association created in 2019. According to the spin-in model, a signed agreement ensures that the startup spin-in TRUSTLESS.AI and Seevik Net will be mandatorily owned and controlled by the TCCB - via an option by TCCB to buy 100% of its shares at precisely-set non-speculative conditions - in order to leverage private sector innovation while ensuring a highly democratic and multi-national long-term control of such a sensitive transnational democratic infrastructure, such as the German DoD Herkules project, but multinational.
The initial version of Seevik Net will derive from the hardening and integration of battle-tested open-source IT stacks, via a resilient consortium of carefully-vetted technical partners in suitable nations, which will include (a) seamlessly portable 2mm-thin client devices, carried in custom leather wallets (video) or embedded in the back of smartphones (video), with special 3rd party apps; (b) interoperable messaging and social apps for mainstream stores, (c) a custom private cloud, made up of decentralized nodes running on TCCB client devices, and multi-national network of hosting rooms according to our TCCB Cloud process.
The TCCB Cloud process, a component of the Trustless Computing Paradigms, prescribes that all sensitive data and code is stored in at least 4 TCCB hosting rooms in diverse nations part of at least 2 different military/intelligence alliances, and approval by a TCCB Jury of 5 random-sampled citizens - for a local lawful access request - and by such jury executing decision by an international TCCB Judicial Board - for international ones.
What makes us think that such front-door mechanism would be secure-enough when most publishing experts say it not possible? We’ve devoted a huge amount of work on our solution, and even hosted eight Free and Safe in Cyberspace conferences around the world - focused exactly on evolving and detail such solution with over 100 experts. This resulted in a detailed academic Position Paper for the Trustless Computing Certification Body, presented during the 5th Edition, in Berlin in 2018, that details our approach to IT security and front-door access, and compares it against decades of expert papers on the subject by leading US/UK experts.
The initiative will eventually be opened for joining to all nations on fair and equal basis.
Milestones, Traction & Roadmap
During our 8th Edition of our Free and Safe in Cyberspace conference held last June 2021 inGeneva/online - after previous editions in Brussels, Berlin, New York, Geneva and Zurich - we finalized the Trustless Computing Paradigms, and the statute of the Trustless Computing Certification Body ("TCCB") - together with World-class speakers, including top IT security experts, the former top cyber diplomats of USA and Netherlands, and executives of top EU banks.
The certification bodies for top secret IT of Austria and Italy (German BSI equivalents) have been governance R&D partners since 2015-2016 EU funding proposals for TCCB, together with EOS the largest EU cyber security industry association and top global tech partners. In recent years and months, we have engaged at top officials at security agencies, foreign office and IT security standardization agencies of EU and "like-minded" nations, including especially Germany, Italy, Austria, but also Israel, USA, Switzerland and UK, for their interest to join as partners of TCCB, users of Seevik Net and/or participate as investors in our startup "spin-in" via their cyber-only state-close VC firms. In recent months initial interest from Romania, Poland.
In recent weeks and months, we have presented custom proposals for Germany, and for Liechtenstein and for Qatar and Israel - small nations with rare strategic autonomy - via recent meetings in DC, London, Munich, and Vaduz, and coming ones in Doha and Tel Aviv. We recently received substantial top-level interest from the United Nations to develop the TCCB inside it as per this proposal, also via a new "voluntary fund" being set up by the UNICC.
We aim this Fall 2022 to have three or more leading nations having agreed join, by agreeing to meet in a founding process via closed-doors and public meetings (online and offline) to revise TCCB statute/governance and the Trustless Computing Paradigms ending with the 9th Edition of our Free and Safe in Cyberspace, to he held next Fall 2022 in a yet-to-be-determined EU capital, and move to the implementation phase to go live in 2024 with TCCB and Seevik Net. So far we received substantial interest from several nations, especially a few larger EU nations, like- minded third countries, as well as US and Israel.
Proposed solutions by human rights organizations
Nearly all suggestions by organizations like Amnesty International, Electronic Frontier Foundation or European Data Protection Supervisor proposed to solve (or sufficiently mitigate) the problem of widespread illegitimate spying on mobile phones revolve around moratoriums, outlawing, regulating state-grade hacking tools, and generic calls for improving the security of devices.
Outlawing the sale of spyware by western governments or firms to other nations would instead be disastrous, making so that client nations would purchase spyware from entities that are closer to adversary nations and criminals, increasing the power of those to spy all, and spy the spies.
Proper regulation could and should surely be enacted, especially in technical and procedural accountability in the development, deployment and use of such systems, but its impact would be minimal under the best scenarios, given the complexity of the context.
Neither would do anything to solve the root causes of the chronic insecurity of all mobile devices, while the proposed mitigations would mostly result in empowering criminals and enemy nations.
Case for US and Israel to join and co-lead the TCCB
In dedicated page, we make a similar case for nations-states to join the TCCB, focused on generic nations.
Yet, in the West, the US and Israel, and partly other “five-eyes” countries, and UK, Germany and France - are in a different position from other western and third-nations. In fact, they have an upper hand in the current hegemonic model for the security and hacking of non-classified but sensitive mobile secure communications.
These nations have much higher capability than other nations to exploit the vulnerabilities on even the most secure iOS or Android smartphones - directly and indirectly through their “private” spyware companies - and in part to protect its officials and citizens against hacking from others.
Why should they then join an initiative that sets international rule-based and fair playing ground and, worse, compromise their ability to defend themselves?
US and Israel current hegemony over mobile security and insecurity.
On the one hand, they both exert an indirect but deep influence over the entrenched global duopoly of Google and Apple mobile app stores and operating systems, over Apple and some of its key staff, and less over secure open end-to-end apps. They do so via regulatory pressures and a variety “proximity” activities, which gives them much deeper visibility and potential influence, over the critical vulnerabilities that “somehow” emerge in those platforms due to hyper-complexity, “odd” architectural choices (e.g. iMessage coding language) and plausibly-deniable compromizations.
On the other hand, due to such influence, resources and talent, Israel and the US lead by far on the capability of exploiting such vulnerabilities through their security agencies, and through indirect control of leading mobile endpoint protections and cyber-security companies, like Crowdstrike, and their ability to sale and oversee nation-states the most effective, pervasive and undetectable spyware systems, like NSO Group, that evade event the best cyber defences.
Overall this model - through leading smartphones, like the iPhone, and open-source deeply-vetted secure messaging solutions like Signal - provides a very good level of protection for well over 99% of citizens that are least targeted, which is great improvement from ten years ago, but it leaves the most targeted 1% and 0.1% that are most in need for security and privacy for their own good and for the resilience of our democratic society.
Through seemingly “private” companies like NSO they get to spy on, limit and control who dozens of nations spy on. Although this clearly deeply abuses the digital sovereignty of governments and citizens in those nations, it has had and has a very substantial role in their success in fighting terrorism, subversion, and grave crimes in their countries and in allied countries, and some also around the World.
Israel, especially, leverages such advantage with great success to protect its national security - which is by far on top of its priorities, for very valid reasons due to highly adversarial international relations in its neighborhood due to deep historical reasons - also through its control over the sale and operation of world-leading Israeli “private” spyware makers, like NSO Group, to increase its threat visibility and to use it as a defensive foreign policy instrument.
A seemingly very difficult case to make
Sure, although the new model we propose is in conformity with current national laws in those nations and with international laws, it appears to be a moon-shot to think that external security agencies from Israel and the US would welcome the fact that IT solutions will go to market that require them to prove their case to a international multi-governmental body - no matter how trustworthy its governance and approval process would be - when they determine there is a need to intercept, for example, a Danish parliamentarian or a Mexican journalist.
Or that their law enforcement and internal secret services would agree to demonstrate that due process was followed (according to national law) to 5 randomly-sampled citizens of their country (and/or elected officials) in order to be able to intercept user of TCCB-compliant devices that is their citizen or present in their territory.
Huge collateral damages of the current model for the US and Israel
The current model and hegemony comes with huge and mounting inefficiencies, collateral damages, and a “boomerang effect” for those leading nations, so it may be worth exploring it there may be a better alternative model, like ours, that would eliminate or radically mitigate those effects, and overall be most convenient for such nations and also for the narrower goals of their security agencies.
Even though they have the upper hand in the current scenario, they are suffering from huge collateral damages that are mining their own democratic systems. Involuntarily, they have ended up weakening the technologies, procedural safeguards and oversight processes of the IT systems that are most critical in sustaining democratic society, such as (a) the mobile devices used by even their top elected officials, parliamentarians, ministers, as well as (b) the targeted hacking systems used to by the police.
This is even more evident last February with a scandal involving NSO Group, Israeli police, and alleged spying of Israeli citizens including the son of the former Israeli prime minister, which was followed by the unattributed hacking of the Spanish prime minister and defence minister. It has become clear that every elected official or citizen not only abroad but also in their country is hackable by who knows who, inside or outside their institutions. In addition, sometimes they “go dark” and the evidence they acquire is often unreliable, and not accepted by their highest courts.
Eight key arguments as to why Israel and the US would benefit from TCCB
Let me list below eight key arguments why Israel or US, counterintuitively, would greatly benefit overall by joining and co-leading the Trustless Computing Certification Body and Seevik Net as opposed to relying only on the current failed model.
First, they would ensure a much higher certainty, integrity, attribution capability when investigating users of users TCCB-compliant systems, foreign and domestic, than they currently have when investigating current IT systems with the current model.
In fact, while their security agencies would “by definition” lose the arbitrary capability to hack into TCCB-compliant systems (which will be designed with the state purpose of being impregnable to such acts) - when legitimately authorized - they will:
(A) have certainty of prompt access, without the risk of “going dark” or being unable to hack, and independently from the availability to assist of other nations or firms; and
(B) obtain more solid and forensic-friendly evidence that is much more reliable and that will be accepted by the highest national courts, unlike that obtained via targeted hacking which does not stand in court in Germany, Italy and France.
Second, they would expand and improve existing multilateral and bilateral agreements whereby Israel and US, as other friend nations, ask each other's permission to allied host nations when having to spy on targets that are citizens of an ally country via an obscure complex web of agreements that are oral, software-coded or written, such as MLATs, Club of Berne, 5-9-15 eyes.
For example, we recently learned there are “rules” in place for at least few years that technically prevent any nation-state client of NSO group to hack target users with a US number or while they are on US territory. Following the scandals in October 2021, such rule was extended Israel, the United States, Canada, Australia, New Zealand and the United Kingdom, and France. To be fair and coherent, following the same rational should that be extended to other allied, friend and non-adversarial nations, both for NSO and other “private” spyware as well as state hacking capabilities?
Third, they would radically mitigate the problem whereby their current target hacking capability, direct and through private firms, produces unreliable and untrustworthy evidence, since client devices could have been hacked by others and do not support forensic, as it was highlighted by Rami Efrati, former Head of Cyber Division of the Prime Minister Office of Israel, during a recent university lecture (min 9.35).
In fact, evidence so acquired via state trojan is structurally contested by highest civilian courts in Germany and France, as well as in Italy. Often parallel construction is used to mitigate such problem, but creates big others of its own. Requests to TCCB instead are approved even in 1-2 hours, if urgent, and produce much cleaner evidence.
Fourth, they would radically increase both the protection of legal communications and the accountability of illegal communications for their most sensitive law-abiding citizens and organizations, including elected officials, journalists, business leaders, activists, as well as their reference organizations.
TCCB would radically increase protection from politically-motivated extortion, blackmail, manipulation, or profit-motivated extortion, ransomware and trade secret spying.
Provided that key elected and appointed officials, and their close personal and professional associates, are mandated to use such devices, TCCB could serve as a way to better exercise accountability and national and investigative powers over grave activities aimed at subverting the democratic constitution, as we’ve seem happen in Germany and the US recently. as we outline in this post under "Germany's internal fight against far-right subversion".
They would radically mitigate the problem of their own elected officials being spied on and blackmail by who knows who.
Over the last decade, in an unforeseen huge “boomerang effect” those same weaknesses and vulnerabilities in the Internet infrastructure have been used by adversary nations, and internal authoritarian forces to wreak havoc, compromising democratic stability and national security.
Any US or Israeli parliamentarian and their close associates - and even the son of Israel prime minister or a US presidential candidate - can be hacked undetectably for months or years on hand. Even worse, the fact that this is often not be discovered, non detectable, and when discovered it is nearly impossible to ascertain who did it, fosters deep division and mistrust with their societies where everyone is an accuser and victim, and mines citizens’ trust in the democratic institutions citizen, creating an untenable situation that could lead Israel down the similar paths as the US democracy.
Fifth, they would mitigate the huge collateral damage of unwittingly fostering a huge cyber crime business, by fostering a billion dollars zero-days market for vulnerabilities, and creating the conditions for leaks like Vault 7 and Shadow Brokers, whereby state-grade hacking tools end up in the Dark Web.
Even the most sophisticated state-grade malware, protected with multiple sophisticated layer of “obfuscation” ends up being “decompiled” by state and non-state actors - as it happened to Finfisher last year - that find them in a victim device, enabling non-state entities of all kinds to re-use them, often leaving no trace afterwards, and with no way to assess the scale of their hacking, and who did it, creating a real Wild West.
Sixth, they would retain the threat visibility and influence that they currently have on third and allied nations through their undue control over the dominant mobile device, platforms, cybersecurity solution and spyware - especially for Israel towards Middle East governments to reduce terrorist and Iran threats - via the careful governance and socio-technical design of our new trustworthy international body, the Trustless Computing Certification Body.
For threat visibility, the TCCB would radically minimize the risk that legitimate cyber-investigations - that one of those nations deem needed, legal and proportionate - will not be approved by the TCCB International Judicial Board, or impossible to exercise for any reasons, even those involving international communications of a nation’s leader.
For the influence, US and Israel could benefit from moving from a positions of deceitful “hard cyber power” over their allies and third-nations to a new model of “soft cyber power”. Move from providing third-nations the ability to hack indiscriminately to giving them the ability to protect legitimate communication and make accountable illegitimate ones.
Seventh, they would repair and relaunch their reputation, trustworthiness and leadership towards allied and third nations - especially after the US NSA revelations of 2013 and the NSO revelations of the last few years - about large-scale unwarranted abuse of nation state clients of NSO Group to spy on journalists and even prime ministers of allied countries, and for making us all (through their bug-door model) more exposed to cyber criminals of all kinds that somehow gain access to the most powerful hacking capabilities.
A leadership by example rather than coercion. A leadership among nations with equal dignity. More carrot and less stick. Affirm a model whereby advancing diplomatic, geopolitical and economic interests can be done while also promoting of peace, freedom, democracy and safety.
They would increase their ability to counter the rise of authoritarianism at home and abroad, by have more democratic investigative visibility into internal subversive activities, as well as more coherently project a leadership by example of a model of digital society that is coherent with western democratic values.
They would be recognized by other nations as co-leaders in promoting peace and fair and effective global cooperation- within and across alliances, having a participating to building nothing less than the new de-facto global standard state-of-the art for sensitive and diplomatic digital communications.
Eight, they would join an initiative that aligns as natural development of the very complex history of attempts by the US to find a solution to this conundrum. It was 1991 when a young Joe Biden, as Chairman of the Senate Judiciary Committee, introduced a bill called the Comprehensive Counter-Terrorism Act, that stated aspirational goals for a front-door access mechanism: "It is the sense of Congress that providers of electronic communications services and manufacturers of electronic communications service equipment shall ensure that communications systems permit the government to obtain the plain text contents of voice, data, and other communications when appropriately authorized by law."
In such bill, Joe Biden did not specify "how" those providers should "shall ensure that communications systems permit the government to obtain the plain text contents of voice, data, and other communications when appropriately authorized by law."
While still correct to this day, the overly generic and minimal nature of the proposed safeguards and requirement, and the prevailing draft implementations of such bill, lead a group of digital rights experts and activists to foresee that ill-thought implementations of such law would have curtailed the freedoms they had just gained for themselves and all citizens with such new encryption protocols and software while doing nothing to stop criminals.
It was Biden's bill, and the looming threat that this newly-found strong encryption would be outlawed, that Phil Zimmermann wrote at the time "led me to publish PGP electronically for free that year.". This open technological solution suddenly enabled anyone in the world to communicate securely, even from US remote interception.
Those fears of those digital rights experts and activists proved to be exactly right. As the use of algorithmically unbreakable encryption kept spreading, in 1993, the Clinton Administration developed a system hardware component, the Clipper Chip, that was promoted and encouraged to be inserted (initially on a voluntary basis) in US human electronic communication devices and systems, to ensure remote access by the government, when authorized by due legal process.
The wide availability of open source algorithmically unbreakable encryption software forced a shift in the western security community whereby they had to move on to break all IT and IT standards to retains the interception capabilities that they had back when they could break all encryption in transit.
Last October 2020, the US, UK, Australia, New Zealand, Japan, and India, published a joint International Statement: End-To-End Encryption and Public Safety, issuing a call to IT providers, NGOs, and stakeholders to find a solution to the problem of encryption technologies hindering law enforcement and security agencies from detecting and preventing grave crimes by individuals and nation-states. In the following November, a Draft Resolution of the Council of European Union was revealed, which was very similar to such a Statement, and literally identical to it in key provisions.
call on civil society, industry and academia to find a solution that enables lawful access requests that are not only legal, but also “necessary and proportionate, and is subject to strong safeguards and oversight." adding key requirements that were missing in the original bill by US President Joe Biden in 1991.
This novelty raises hopes that new mechanisms, standards, certifications, and bodies could be created - reserved for IT systems for human communications conceived for the highest levels of security - that apply such new stringent requirements to mechanisms that can both ensure legitimate lawful access as well as radically raise the level of security and privacy of those systems.
Ninth, they would be able to affirm a new leadership based on the principles of democracy and fair and effective international relations, communications and cooperation, via win-win solutions whereby national security is increase while and by advancing our democratic and liberal societal values.
For all these reasons, we believe that by co-leading other nations to build the TCCB and Seevik Net, the US or Israel could lead to enact a new model of democratic digital society that is finally coherent with their liberty and democratic principles, creating an healthy constructive competition with China, and other fast rising autocracies, for the hearts and minds of world citizens, and promote therefore security, peace, democracy and freedom, at home and abroad.